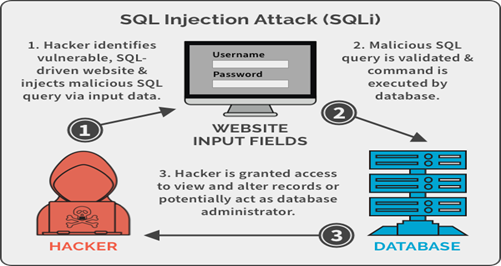
SQL injection is a web security vulnerability that allows the attackers to interfere with the queries that an application makes to its databases. It allows the attacker to grab the data that cannot be retrieved further.
In many cases the attacker can delete the data permanently or make effective changes in them. Many high profile data breaches that occurred recently were due to SQL injection.
This attack can exist for a long time. When the attacker successfully injects malware into an organization’s system, it may take time to track it down oreven may go unnoticed for an extended period.
SQL injection is one of the simple and ethical hacking techniques that need an application that uses a database. Generally a web application receives data from the users and stores in the database
or vice versa. In both these case, a query is generated. The cyber hacks manipulates this query to carry out malicious activities.
Once the hacker successfully manipulates the query, it is sent to the database, executed there and relevant results are returned.
Patterns of SQL injection attack
- Retrieving hidden data
Here you can modify an SQL query to return additional results.
- Subverting application logic
In this you can change a query to interfere with the application’s logic.
- UNION attacks
Where you can retrieve data from different database tables.
- Examining the database
Here you can extract information about the version and structure of the database.
- Blind SQL injection
The results of a query you control are not returned in the application’s responses. SQL injection was considered one of the top 10 web application vulnerabilities of 2007 and 2010 by Open Web Application
Security Project. In 2013 SQLI was rated the number one attack on the OWASP top ten
Sub Classes of SQL injection
- Classic SQLI
- Blind or interference SQL injection
- Database management system-specific SQLI
- Compound SQLI
Types of SQL injections
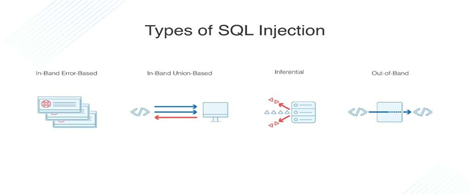
SQL generally falls under three categories: In-band SQLI (classic), Inferential SQLI (Blind) and Out-of-band SQLI. This classification is based on the methods they used to access backend data and their damage potential. In In-band SQLI the attacker uses the same channel of communication to launch their attacks and to gather their results. This is the most common type of SQLI attack. This is
further divided into two, Error based SQLI and Union based SQLI.
In the case of Inferential SQLI the hacker sends payload malware to the server to observe the behaviour and structure of the response. Here the data is not transferred from the website database to the attacker, hence the attacker cannot see the information about the attack in-band.
Out-of-band SQLI can be carried out only when some features of the database server are enabled. Here the attacker can’t use the same channel to launch the attack and gather information or a server is too slow or unstable for these actions to be performed.
Consequences
- Confidentiality: As these attacks holds sensitive data, loss of confidentiality is one of the major problem with SQLI.
- Authentication: If poor SQL commands are used to check user names and passwords, it may be possible to connect to a system as another user with no previous knowledge of password.
- Authorization: If authorization information is held on a SQL database, it may be possible to change this information through the successful exploitation of a SQL Injection vulnerability.
- Integrity: Just as it may be possible to read sensitive information, it is also possible to make changes or even delete this information with a SQL injection attack.
Stay Away from SQL injection attacks
- Stop using dynamic queries
- Integrate security checks (input validation)
- Provide parameterized database queries
- Use stored procedures
- Use the input validations of a whitelist
- Use captcha queries
Happenings
- In February 2002, Jermiah Jacks discovered that Guess.com was vulnerable to an SQL injection attack, permitting anyone to construct a properly crafted URL to pull-down 200,00+ names, credit card numbers and expiration dates in the site’s customer database.
- On March 29, 2006 a SQL injection attack was discovered in one of the tourism sites of Indian Government