Network attack is an attempt to gain unauthorized access to an organization’s network with the objective of stealing data or perform other malicious activity.
Every developing organization will have a large and complex network with multiple end points. This benefits and ensures the smooth working of the company. But as far as security is concerned, this could be a major threat.
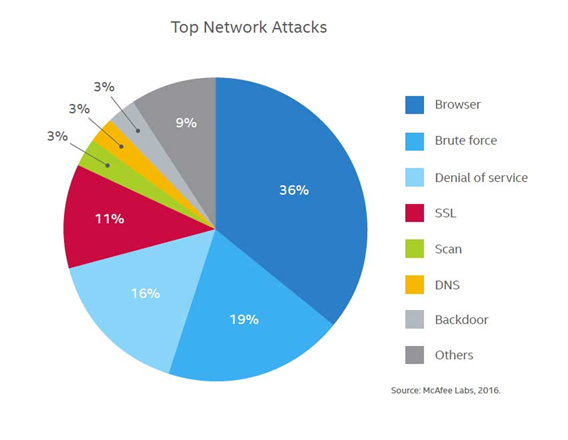
A bit more about Network attacks
The malware associated with network attacks are free to move from one system to another without the interference of an external hacker. This causes severe damage without our knowledge.
Some of the prevalent types of network attacks today include malware, virus, worm, botnet etc.
Malware is dangerous software which is designed to disrupt or damage a computer system. Most of the malwares today are self-replicating. Once it affects one host, from that host it seeks entry into other hosts over the internet, and from the newly infected host it gains entry into multiple hosts making it spread exponentially fast.
Virus is a kind of malware which requires user interaction to infect a device. Most of the virus attacks are through email attachments. When the target opens the mail the malware gets activated and runs the system.
Worm on the other hand can reach the target without explicit user interaction.
Botnet is a network of private computers infected with malicious software and controlled as a group of owner’s knowledge.
General categorization of network attacks
- Passive attacks
In this kind of attacks, the malware gains the access to personal information and steals sensitive content without disturbing the data or damaging them. The data remains intact. This type of attack is an easy walk-in for the hackers.
- Active attacks
In this category there are chances that the malware destroys or deletes the data after gaining the access. They may encrypt the entire data.
Types of network attacks
- Unauthorized access
This attack happens when we set a weak password or lack protection against weak engineering. As the name suggests, the attackers enters your system without any permission or authorization.
- Distributed Denial of Service (DDoS) attacks
In this kind of attacks the hackers create large compromised devices and use them to false traffic the targets network and servers.
- Man in the middle attacks
Here the attackers act as a mediator between user network and external sites or within the networks. Here the cyber hacks can obtain user credentials and hijack their sessions.
- Code and SQL injection attacks
There are websites that accepts the input of the users and fails to destroy them after use. Attackers use this as an opportunity to fill out a form or make an APL call passing malicious code instead of expected data values.
- Privilege escalation
Once the hacker is into your device, he can use privilege escalation technique to expand his reach. The expansion can be both vertical and horizontal. Horizontal escalation means gaining additional access
and vertical escalation means gaining higher level privilege of the same system.
- Insider threats
Insider malware is not an external infection but rather an internal one. These threats are difficult to access but some new technologies like User and Even Behavioural Analytics (UEBA) can help to identify suspicious or anomalous behaviour.
Cases reported
- Adobe
Date: October 2013
Impact: 153 million user records
As reported in early October of 2013, the hackers have stolen nearly 3 million encrypted customer credit card records, plus login data for an undetermined number of user accounts.
- Adult Friend Finder
Date: October 2016
Impact: 412.2 million accounts
This breach was particularly sensitive for account holders because of the services the site offered. The stolen data spanned 20 years on six databases and included names, emails, addresses and passwords.
- Canva
Date: May 2019
Impact: 137 million user accounts
In May 2019 Australian graphic design tool website Canva suffered an attack that exposed email addresses, usernames, names, cities of residence and salted and hashed with bcrypt passwords of 137 million users.
How to stay away from networks attacks
First and the most important thing is that you segregate your network. Divide networks into zones based on security requirements. This can be done using Virtual Local Area Networks (VLANs).
In case of an organization, never allow the users to access the internet unchecked. Setup transparent proxy and monitor every activity using them. Always look out for bot activities and make sure every outbound connection is human performed.
Place Firewall at every junction of network zones and not just network edges.
Make sure you have the complete visibility of the network operations. Combine data from different security tools to get a clear cut picture of what is happening on the network. Cynet 360 is an integrated security solution offering advanced network analytics.
Cynet 360 blocks suspicious behaviours, malwares, UBA, deception and uncovers hidden threats.
Network attacks are real. Stay conscious and protected!

