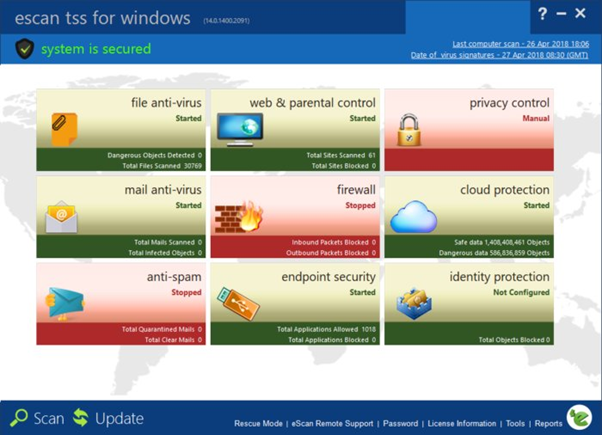
Cyber threats are increasing significantly in the modern world. Technology and internet has taken away almost every sector of the society. Due to the same reason, people and organizations are being vulnerable to cyber-attacks. Internet is an unavoidable part of everyone’s life. The benefits of internet are largely praised by everyone, but little do they know that it acts as a connecting bridge between the users and the threat actors. Most of the dangerous malwares have been spreading through internet.
To protect our personal information and to secure our privacy, we should have a strong and reliable security software.
Immunet can protect you from all the emerging threats and safeguard your sensitive information.
Immunet works with the help of cloud computing system and it is one of the finest security solutions available in the market. It mainly functions on Windows computers and they are user-friendly. The software stays active over a network where about two million users utilize them to create a better defence mechanism. If any one of the user within the network is attacked, the software gathers information about the malware and ensures protection to all the other users from that malware.
Advantages
- They provide real-time threat detection and they have a manual update system.
- They are compatible with 32-bit and 64-bit versions of Windows.
- They need small amount of RAM to function.
- They can be used with other anti-virus programs.
Disadvantages
- It doesn’t have email scanning feature.
- They don’t detect threats from external drives.
- There are variations in function during offline.
Basic features
You can install Immunet software within 60 seconds and does not occupy more than 100MB of space.
- Once Immunet is installed it automatically runs Flash scan and checks for malicious outsiders in the running process and starts the function of registry keys.
- The Block Mode feature helps to block newly installed applications if any threat is found within the program. Only safe applications are granted permission inside the system.
- They ensure immediate response to viruses, malwares, spywares, ransomwares, adwares etc.
- The custom scan helps to scan specific files or folders.
- The schedule scan feature helps you to run scans according to your schedule. It can be daily, weekly or monthly. Schedule scan has the option to perform full, flash or custom scan.
- Without activating on-demand or scheduled scans, the software automatically calls out to scan the system for malicious threats like Trojans and Keyloggers.
- If they found any threat while scanning, Immunet quarantine them separately.
- There are possibilities where the software can detect some Windows files as infected ones. To avoid this confusion, select the file, folder or file extension to add to the exclusion list so that you don’t lose important files.
- Gaming mode enables the users to stay away from unnecessary notifications.
- There is always a record maintained within the software that saves all the activities done by the software like running scans, detecting threats, blocking and quarantining files. You can go through them if necessary and there are options to sort the activities according to the date and time.
- You can manually activate or deactivate the cloud detection engines like ETHOS and SPERO.
- While you are offline, ClamAV engines looks out for threats.
- They are compatible with Windows 7, 8, 10 and the server 2016/2012/2008 R2.
Immunet is powered by an open source ClamAV scanner. They have an efficient user-friendly front end which is available only as definition database in other anti-virus softwares. Immunet provides options to view the CPU performance and display memory from the product dashboard. Antivirus software utilizes power and memory of the system to function. So it better to have an idea of how much memory and power it is using.
Immunet has a separate social network called Immunet Community. Through this community, users exchanges virus data so that the software can analyse them and no one else gets affected by the virus.
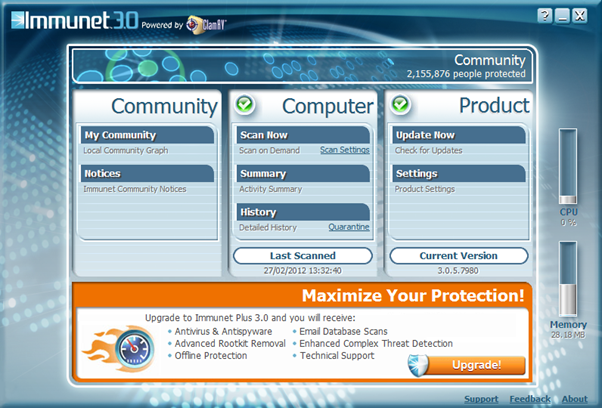
Immunet is one of the lightest anti-virus software available within a megabyte. While considering the entire database of ClamAV, it’s just around 20MB. This helps the software to act quickly and keep updated.
Immunet is a free anti-virus software which can be downloaded free from their official website www.immunet.com